This week the Rogue Blog reports a strong surge in a different type of rogue, one that pretends to be a system utility. Typical scareware pretends to be antivirus software, "finds" all kinds of threats, and demands that you pay before it will clean up the pretend problems it found. Utility-style scareware follows a similar pattern. It pretends to find errors on your system such as disk fragmentation or file system integrity problems. Naturally the scan is free; naturally you have to pay if you want to fix the alleged system problems.
The Rogue Blog post pointing out this trend includes numerous screenshots and identifies many of the culprits by name. UltraDefragger, ScanDisk, and WinHDD are among the real-sounding names used by current fraudulent system utilities.
How can you distinguish a fake optimization tool from a real one? If you see a report from a utility that you never installed and never launched, it's probably a fraud. If the utility comes advertised in a spam message, Sunbelt suggests you avoid it. The rogues invariably display dire warnings about system problems, but don't reject every warning. A legitimate disk utility might do the same if your system is truly failing.
Here's an odd one: apparently these rogue utilities will often tell you that you must update your browser to a version earlier than what you're actually running.
If you're careful you can avoid getting burned. Don't ever rely on a third-party system utility that you didn't install or launch, as it's almost certainly a fraud.
Your antivirus software or security suite should protect you from rogues of any kind, providing you keep it up to date. And when you go shopping for disk tools do a little research to make sure they're legitimate. Check PCMag.com for reviews, to start, and Google the name to see if others are reporting problems. If you're still not sure, a visit to the Rogue Blog should clear up any confusion.
Originally posted on Yahoo News
PC Tools, Utilities, software downloads, tech news and software tips
Friday, December 17, 2010
Thursday, November 25, 2010
Tech Scams to Avoid This Holiday
The holiday shopping season is a great time to get tech products at discounted prices, but it also creates a golden opportunity for the Web's scam artists. The FBI, McAfee, the Better Business Bureau and F-Secure are all warning about cybercriminals who will try to take you for a ride this holiday season. Here are their most pertinent warnings and tips for staying safe:
The Infamous Free iPad
Bogus free iPad offers started popping up immediately after Apple's tablet went on sale, and they've since been banned from Facebook. Still, you might see similar offers around the Web, McAfee says, prompting you to buy other products as a condition of getting the free iPad. By now, you should realize it's too good to be true.
Gift Card Scams
That free $1,000 gift card offer you saw on Facebook? Bogus, of course. McAfee says that cybercrooks lure people into giving away their personal information or taking quizzes in exchange for these cards, which never arrive. The information is then sold to marketers or used for identity theft.
The FBI also says to use caution when purchasing gift cards through auction sites or classified ads. These can be fraudulent, and you won't get your money back. Buy directly from retailers instead.
Bogus Auctions and Classifieds
Here's a particularly tricky scheme pointed out by the FBI: On auction and classified sites, fraudsters use their own order forms to get payment details from holiday gift buyers. Then, they charge the victim's credit card and use a stolen credit card to buy the actual item, which is sent directly to the victim. In other words, you'll still get the product, but you might be liable for receiving stolen goods. To avoid this scam, be sure to use legitimate payment services like Paypal instead of providing money directly to the seller.
The feds also warn of a related scam for free or reduced-price shipping offered on auction and classified sites. The fraudsters provide fake shipping labels to the victim, and the product ends up being intercepted in transit, never delivered to its destination.
Malicious websites
For cybercriminals, spamming Google with bogus holiday gift pages is a yearly tradition. These pages could be loaded with malware or payment forms intended to steal your identity. F-Secure has created a list of what it thinks will be the highly targeted search terms this year, including Kinect for Xbox, Call of Duty: Black Ops, Amazon Kindle and Apple iPad.
Visit retailers' websites directly when possible, use Internet security software if you must and always check for "https" in the URL bar before ordering online to ensure that the page is secure.
Wi-Fi Hackers
Public Wi-Fi networks will get a workout this holiday season as people travel, McAfee notes. This is especially true with Google offering free Wi-Fi on domestic flights from three major airlines. Check out our security tips from Google's free Wi-Fi offer at airports last year, most of which are still relevant in the skies. Number one tip: Avoid shopping and paying bills over a public network.ls over a public network.
Originally posted on PCWorld
The Infamous Free iPad
Bogus free iPad offers started popping up immediately after Apple's tablet went on sale, and they've since been banned from Facebook. Still, you might see similar offers around the Web, McAfee says, prompting you to buy other products as a condition of getting the free iPad. By now, you should realize it's too good to be true.
Gift Card Scams
That free $1,000 gift card offer you saw on Facebook? Bogus, of course. McAfee says that cybercrooks lure people into giving away their personal information or taking quizzes in exchange for these cards, which never arrive. The information is then sold to marketers or used for identity theft.
The FBI also says to use caution when purchasing gift cards through auction sites or classified ads. These can be fraudulent, and you won't get your money back. Buy directly from retailers instead.
Bogus Auctions and Classifieds
Here's a particularly tricky scheme pointed out by the FBI: On auction and classified sites, fraudsters use their own order forms to get payment details from holiday gift buyers. Then, they charge the victim's credit card and use a stolen credit card to buy the actual item, which is sent directly to the victim. In other words, you'll still get the product, but you might be liable for receiving stolen goods. To avoid this scam, be sure to use legitimate payment services like Paypal instead of providing money directly to the seller.
The feds also warn of a related scam for free or reduced-price shipping offered on auction and classified sites. The fraudsters provide fake shipping labels to the victim, and the product ends up being intercepted in transit, never delivered to its destination.
Malicious websites
For cybercriminals, spamming Google with bogus holiday gift pages is a yearly tradition. These pages could be loaded with malware or payment forms intended to steal your identity. F-Secure has created a list of what it thinks will be the highly targeted search terms this year, including Kinect for Xbox, Call of Duty: Black Ops, Amazon Kindle and Apple iPad.
Visit retailers' websites directly when possible, use Internet security software if you must and always check for "https" in the URL bar before ordering online to ensure that the page is secure.
Wi-Fi Hackers
Public Wi-Fi networks will get a workout this holiday season as people travel, McAfee notes. This is especially true with Google offering free Wi-Fi on domestic flights from three major airlines. Check out our security tips from Google's free Wi-Fi offer at airports last year, most of which are still relevant in the skies. Number one tip: Avoid shopping and paying bills over a public network.ls over a public network.
Related articles
- Latest McAfee warns of "The 12 scams of Christmas" (helpwithdebtnow.com)
- Bogus iPads Top 12 Scams of Christmas (cultofmac.com)
Friday, November 19, 2010
Smart Online Behavior Prevents Malware
Malware is a term used to describe a broad category of damaging software that includes viruses, worms, trojan horses, rootkits, spyware, and adware. The effects of malware range from brief annoyance to computer crashes and identity theft. Malware is easier to avoid than it is to remove. Avoiding malware involves a two-part strategy. Follow these guidelines for staying safe.
The single biggest factor in preventing a malware infection on your PC is you. You don't need expert knowledge or special training. You just need vigilance to avoid downloading and installing anything you do not understand or trust, no matter how tempting, from the following sources:
From a website: If you are unsure, leave the site and research the software you are being asked to install. If it is OK, you can always come back to site and install it. If it is not OK, you will avoid a malware headache.
From e-mail: Do not trust anything associated with a spam e-mail. Approach e-mail from people you know with caution when the message contains links or attachments. If you are suspicious of what you are being asked to view or install, don't do it.
From physical media: Your friends, family, and associates may unknowingly give you a disc or flash drive with an infected file on it. Don't blindly accept these files; scan them with security software. If you are still unsure, do not accept the files.
From a pop-up window: Some pop-up windows or boxes will attempt to corner you into downloading software or accepting a free "system scan" of some type. Often these pop-ups will employ scare tactics to make you believe you need what they are offering in order to be safe. Close the pop-up without clicking anything inside it (including the X in the corner). Close the window via Windows Task Manager (press Ctrl-Alt-Delete).
From another piece of software: Some programs attempt to install malware as a part of their own installation process. When installing software, pay close attention to the message boxes before clicking Next, OK, or I Agree. Scan the user agreement for anything that suggests malware may be a part of the installation. If you are unsure, cancel the installation, check up on the program, and run the installation again if you determine it is safe.
From illegal file-sharing services: You're on your own if you enter this realm. There is little quality control in the world of illegal software, and it is easy for an attacker to name a piece of malware after a popular movie, album, or program to tempt you into downloading it.
Remove Malware With the Right Software
Chances are that no matter how careful you are, you will be infected some day. That's because malware is designed to sneak onto your computer in ways you can't possibly foresee. Enlist the help of the following software:
An updated operating system: Use Windows Update. Take advantage of its ability to automatically notify you of updates, or better yet, to automatically download and install updates.
An updated browser: No matter which browser you use, keeping it current is vital to preventing infection. Take advantage of your browser's pop-up blocking, download screening, and automatic update features.
Antivirus software: You must run an antivirus program to be safe. Keep it updated, turned on, and schedule a scan to run at least once a month. (Don't run two antivirus programs; they will interfere with one another.)
Anti-malware: Also called anti-spyware, many antivirus applications include an anti-malware component. If yours does not, install and use a standalone anti-malware program that does not conflict with your antivirus program. Keep it updated.
Firewall: If you aren't running a third-party firewall, use Windows Firewall. (Don't run two firewalls at once; they will interfere with one another.)
Spam filter: If your e-mail program is not adequately filtering spam from your in-box, consider additional spam filtering software. If your security software is a security suite, spam filtering may be a feature that you need to switch on.
The single biggest factor in preventing a malware infection on your PC is you. You don't need expert knowledge or special training. You just need vigilance to avoid downloading and installing anything you do not understand or trust, no matter how tempting, from the following sources:
From a website: If you are unsure, leave the site and research the software you are being asked to install. If it is OK, you can always come back to site and install it. If it is not OK, you will avoid a malware headache.
From e-mail: Do not trust anything associated with a spam e-mail. Approach e-mail from people you know with caution when the message contains links or attachments. If you are suspicious of what you are being asked to view or install, don't do it.
From physical media: Your friends, family, and associates may unknowingly give you a disc or flash drive with an infected file on it. Don't blindly accept these files; scan them with security software. If you are still unsure, do not accept the files.
From a pop-up window: Some pop-up windows or boxes will attempt to corner you into downloading software or accepting a free "system scan" of some type. Often these pop-ups will employ scare tactics to make you believe you need what they are offering in order to be safe. Close the pop-up without clicking anything inside it (including the X in the corner). Close the window via Windows Task Manager (press Ctrl-Alt-Delete).
From another piece of software: Some programs attempt to install malware as a part of their own installation process. When installing software, pay close attention to the message boxes before clicking Next, OK, or I Agree. Scan the user agreement for anything that suggests malware may be a part of the installation. If you are unsure, cancel the installation, check up on the program, and run the installation again if you determine it is safe.
From illegal file-sharing services: You're on your own if you enter this realm. There is little quality control in the world of illegal software, and it is easy for an attacker to name a piece of malware after a popular movie, album, or program to tempt you into downloading it.
Remove Malware With the Right Software
Chances are that no matter how careful you are, you will be infected some day. That's because malware is designed to sneak onto your computer in ways you can't possibly foresee. Enlist the help of the following software:
An updated operating system: Use Windows Update. Take advantage of its ability to automatically notify you of updates, or better yet, to automatically download and install updates.
An updated browser: No matter which browser you use, keeping it current is vital to preventing infection. Take advantage of your browser's pop-up blocking, download screening, and automatic update features.
Antivirus software: You must run an antivirus program to be safe. Keep it updated, turned on, and schedule a scan to run at least once a month. (Don't run two antivirus programs; they will interfere with one another.)
Anti-malware: Also called anti-spyware, many antivirus applications include an anti-malware component. If yours does not, install and use a standalone anti-malware program that does not conflict with your antivirus program. Keep it updated.
Firewall: If you aren't running a third-party firewall, use Windows Firewall. (Don't run two firewalls at once; they will interfere with one another.)
Spam filter: If your e-mail program is not adequately filtering spam from your in-box, consider additional spam filtering software. If your security software is a security suite, spam filtering may be a feature that you need to switch on.
Labels:
malware,
pc security,
spyware
Thursday, November 18, 2010
Identity Theft Misconceptions
A recent survey by Kindsight revealed some misconceptions by internet users what they perceive as identity theft risks.
Anyone living in the modern world can't help but be aware that identity theft is real, and that it's a real problem. But how well do people understand what their own risks are? Not surprisingly, virtually all of those questioned had some understanding of identity theft. However, many had only a limited understanding of just what kinds of behavior put them at risk.
It appears that many consumers still are not entirely sure of what type of activities to avoid, and what they can do to protect their identities online. Five key misconceptions about cybersecurity emerged:
Misconception #1 I’m safe because I never shop online
Misconception #2 I’m safe because I have anti-virus protection
Misconception #3 I’m safe because the website is secure
Misconception #4 I’m safe because it’s easy to recognize fake sites
Misconception #5 Facebook is safe enough; no need to worry
Cybercriminals are becoming more sophisticated and always looking for new and better ways to steal your identity online.
Anyone living in the modern world can't help but be aware that identity theft is real, and that it's a real problem. But how well do people understand what their own risks are? Not surprisingly, virtually all of those questioned had some understanding of identity theft. However, many had only a limited understanding of just what kinds of behavior put them at risk.
It appears that many consumers still are not entirely sure of what type of activities to avoid, and what they can do to protect their identities online. Five key misconceptions about cybersecurity emerged:
Misconception #1 I’m safe because I never shop online
Misconception #2 I’m safe because I have anti-virus protection
Misconception #3 I’m safe because the website is secure
Misconception #4 I’m safe because it’s easy to recognize fake sites
Misconception #5 Facebook is safe enough; no need to worry
Cybercriminals are becoming more sophisticated and always looking for new and better ways to steal your identity online.
Labels:
News,
pc security,
Tech News
Wednesday, November 10, 2010
Optimize Your PC: CCleaner 300
Want to clean and optimize your PC? You've probably heard of CCleaner, arguably the world's most popular tool for doing the job. Developer Piriform just released CCleaner 3.0.
The big news in this update? A native 64-bit version for use with like editions of Windows. Like the last release, CCleaner clears out temporary files, cleans the Windows Registry, erases browser histories, and so on. Version 3.0 also sports new icons, various interface improvements, better support for Google Chrome and Internet Explorer 9, and newly added support for programs like AVG AntiVirus 10.0, Audacity, LogMeIn Hamachi, BitTorrent, and Windows Game Explorer.
I particularly like the way it intelligently scans for cookies you'd want to keep, like those for Google and Yahoo. In short, the ultimate system-cleaning tool just got better. It's still free, thankfully, though you can purchase a priority-support license for $25.
As with any tool of this kind, I strongly recommend making a full system backup and creating a new system-restore point before using it. Better safe than sorry!
Operating Systems: Windows NT, Windows 98, Windows 2000, Windows Me, Windows XP, Windows Vista, Windows 7
The big news in this update? A native 64-bit version for use with like editions of Windows. Like the last release, CCleaner clears out temporary files, cleans the Windows Registry, erases browser histories, and so on. Version 3.0 also sports new icons, various interface improvements, better support for Google Chrome and Internet Explorer 9, and newly added support for programs like AVG AntiVirus 10.0, Audacity, LogMeIn Hamachi, BitTorrent, and Windows Game Explorer.
I particularly like the way it intelligently scans for cookies you'd want to keep, like those for Google and Yahoo. In short, the ultimate system-cleaning tool just got better. It's still free, thankfully, though you can purchase a priority-support license for $25.
As with any tool of this kind, I strongly recommend making a full system backup and creating a new system-restore point before using it. Better safe than sorry!
Operating Systems: Windows NT, Windows 98, Windows 2000, Windows Me, Windows XP, Windows Vista, Windows 7
- License Type: Free
- Price: Free
Labels:
pc performance,
pc tips,
software
Thursday, November 4, 2010
Security Tips for PDF users
The good thing about Adobe's PDF format is that nearly everybody uses it--and if you just need to read those documents, it's free. Sadly, the program's very popularity is what attracts the bad guys. Hackers, say the security experts, look for a "target-rich environment," and with tens of millions of users, Acrobat and Reader fit the bill.
So what can you do to stay secure? I wish I had advice that went beyond the conventional wisdom, but I don't. I contacted security experts at Adobe and Symantec, and they both said pretty much the same thing. Marc Fossi, Manager, Research and Development, Symantec Security Response said this:
1. Consumers should make sure to keep their software up-to-date with all the most recent versions and security patches at all times. An easy way to do this is to ensure that applications are configured to retrieve updates automatically whenever there is a live Internet connection.
2. Using a full security software suite that includes antivirus and intrusion prevention capabilities can also protect against these types of threats.
Sure, Symantec is in the business of selling security software, so naturally they'll tell you to use their product. But in this case, put aside your skepticism and do what the man says. Newer security programs really do filter out lots of malware. And while it may seem utterly obvious, I'll repeat this old chestnut: Don't open attachments from people you don't know.
If you're running version 9 of Reader, you'll be prompted to download a security patch within the next few weeks. Do it.
So what can you do to stay secure? I wish I had advice that went beyond the conventional wisdom, but I don't. I contacted security experts at Adobe and Symantec, and they both said pretty much the same thing. Marc Fossi, Manager, Research and Development, Symantec Security Response said this:
1. Consumers should make sure to keep their software up-to-date with all the most recent versions and security patches at all times. An easy way to do this is to ensure that applications are configured to retrieve updates automatically whenever there is a live Internet connection.
2. Using a full security software suite that includes antivirus and intrusion prevention capabilities can also protect against these types of threats.
Sure, Symantec is in the business of selling security software, so naturally they'll tell you to use their product. But in this case, put aside your skepticism and do what the man says. Newer security programs really do filter out lots of malware. And while it may seem utterly obvious, I'll repeat this old chestnut: Don't open attachments from people you don't know.
If you're running version 9 of Reader, you'll be prompted to download a security patch within the next few weeks. Do it.
Labels:
pc tips,
software tips,
Tech News
Thursday, October 28, 2010
LimeWire music -sharing service shut down
A U.S. federal judge on Tuesday granted the music industry's request to shut down the popular LimeWire file-sharing service, which had been found liable for copyright infringement.
The ruling by Judge Kimba Wood in Manhattan federal court halts one of the world's biggest services for letting consumers share music, movies and TV shows for free over the Internet.
Saying that LimeWire's parent Lime Wire LLC intentionally caused a "massive scale of infringement" involving thousands of works, Wood issued a permanent injunction that requires the company to disable its "searching, downloading, uploading, file trading and/or file distribution functionality.
" Record companies "have suffered -- and will continue to suffer -- irreparable harm from Lime Wire's inducement of widespread infringement of their works," Wood wrote. She called the potential damages "staggering," and probably "well beyond" the New York-based company's ability to pay.
The signed ruling was made available by The Recording Industry Association of America, which represents music companies. It has said Lime Wire has cost its members hundreds of millions of dollars in revenue. A copy of the ruling was not immediately available on the public court docket. Read more
The ruling by Judge Kimba Wood in Manhattan federal court halts one of the world's biggest services for letting consumers share music, movies and TV shows for free over the Internet.
Saying that LimeWire's parent Lime Wire LLC intentionally caused a "massive scale of infringement" involving thousands of works, Wood issued a permanent injunction that requires the company to disable its "searching, downloading, uploading, file trading and/or file distribution functionality.
" Record companies "have suffered -- and will continue to suffer -- irreparable harm from Lime Wire's inducement of widespread infringement of their works," Wood wrote. She called the potential damages "staggering," and probably "well beyond" the New York-based company's ability to pay.
The signed ruling was made available by The Recording Industry Association of America, which represents music companies. It has said Lime Wire has cost its members hundreds of millions of dollars in revenue. A copy of the ruling was not immediately available on the public court docket. Read more
Google Spying?
MPs have accused internet giant Google of deliberately spying on households for commercial gain.
Tory Robert Halfon said it was "hard to believe" that Google could copy millions of computer passwords and email details and "not know what it was doing". And Liberal Democrat Don Foster said it was "not surprising" that the company "want to capture as much of the data as they can to use it for commercial purposes".
Google has admitted "mistakenly" collecting information from wireless networks as its vehicles drove around residential streets taking photographs for its Street View mapping product. The Information Commissioner's Office (ICO), the UK's privacy watchdog, is now investigating the matter.
During a Westminster Hall debate on privacy and the internet, Mr Halfon said: "It's not good enough, as Google have suggested, that the whole thing was an innocent mistake. "That was their line when Street View uploaded images of naked children without the consent and knowledge of those involved. That was their line when a Google engineer was able illegally to access children's private email accounts and telephone records - and then Google took disciplinary action only after parents complained that the engineer had illegally used Google data to harass their children. "I find it hard to believe that a company with the creative genius and originality of Google could map the personal wifi details, computer passwords and email addresses of millions of people across the world and not know what it was doing.
Mr Foster said: "It is for commercial purposes that they (Google) are doing this. Only today we have had revealed the latest figures on the value of e-commerce in this country, which has gone in a very, very short number of years from nothing to £100 billion, which is 7% of the economy of this country - and we all know it's going to rise. So it's not surprising that Google want to capture as much of the data as they can to use it for commercial purposes."
Mark Lancaster, Tory MP for Milton Keynes North, spoke of a women's refuge in his constituency whose need for anonymity had been "ignored" by Google. "Imagine their (potential refugees') great concern when on entering the name of the organisation on Google, a picture of the building the refugees use and also their address appear on the search engine," he said.
Requests to Google to remove the women's refuge from the map had received no response, he added. Mr Halfon called for a "serious commission of inquiry" that would seek to "redress the balance" between the freedom of the internet and users' civil liberties. This commission of inquiry would be composed of members with expertise on civil liberties, the internet and commerce, he said.
Originally posted at Yahoo news UK
Tory Robert Halfon said it was "hard to believe" that Google could copy millions of computer passwords and email details and "not know what it was doing". And Liberal Democrat Don Foster said it was "not surprising" that the company "want to capture as much of the data as they can to use it for commercial purposes".
Google has admitted "mistakenly" collecting information from wireless networks as its vehicles drove around residential streets taking photographs for its Street View mapping product. The Information Commissioner's Office (ICO), the UK's privacy watchdog, is now investigating the matter.
During a Westminster Hall debate on privacy and the internet, Mr Halfon said: "It's not good enough, as Google have suggested, that the whole thing was an innocent mistake. "That was their line when Street View uploaded images of naked children without the consent and knowledge of those involved. That was their line when a Google engineer was able illegally to access children's private email accounts and telephone records - and then Google took disciplinary action only after parents complained that the engineer had illegally used Google data to harass their children. "I find it hard to believe that a company with the creative genius and originality of Google could map the personal wifi details, computer passwords and email addresses of millions of people across the world and not know what it was doing.
Mr Foster said: "It is for commercial purposes that they (Google) are doing this. Only today we have had revealed the latest figures on the value of e-commerce in this country, which has gone in a very, very short number of years from nothing to £100 billion, which is 7% of the economy of this country - and we all know it's going to rise. So it's not surprising that Google want to capture as much of the data as they can to use it for commercial purposes."
Mark Lancaster, Tory MP for Milton Keynes North, spoke of a women's refuge in his constituency whose need for anonymity had been "ignored" by Google. "Imagine their (potential refugees') great concern when on entering the name of the organisation on Google, a picture of the building the refugees use and also their address appear on the search engine," he said.
Requests to Google to remove the women's refuge from the map had received no response, he added. Mr Halfon called for a "serious commission of inquiry" that would seek to "redress the balance" between the freedom of the internet and users' civil liberties. This commission of inquiry would be composed of members with expertise on civil liberties, the internet and commerce, he said.
Originally posted at Yahoo news UK
Tuesday, October 26, 2010
Guide to Your own VPN
How to connect computers over the Internet
There is a way to setup a private connection to your computer at the office/ home from your laptop, the way to do this is to use a Virtual Private Network, or VPN. A VPN is a secure, private network connection or “tunnel” that runs between two or more PC, across the Internet. Even though a VPN’s data travels across a public network like the Internet, it is secure because generally VPN products will make use of very strong encryption.
There are several ways of setting up such a VPN. You can either make use of a specialised consumer VPN router, or install VPN software, which is the more widely used method. There have been some outstanding advances in DIY VPN software over the years, with the entire process being greatly simplified.
LogMeIn Hamachi is one of the better VPN clients I’ve seen. You can get up and running very quickly with almost no configuration needed. This product will let you connect to an entire network and share network drives. Free for non-commercial use.
RealVNC means Virtual Network Computing. It is remote control software which allows you to access a server computer from another one named viewer. The two computers do not even have to be the same type. VNC is freely and publicly available and is in widespread active use by millions throughout industry, academia and privately.
There is a way to setup a private connection to your computer at the office/ home from your laptop, the way to do this is to use a Virtual Private Network, or VPN. A VPN is a secure, private network connection or “tunnel” that runs between two or more PC, across the Internet. Even though a VPN’s data travels across a public network like the Internet, it is secure because generally VPN products will make use of very strong encryption.
There are several ways of setting up such a VPN. You can either make use of a specialised consumer VPN router, or install VPN software, which is the more widely used method. There have been some outstanding advances in DIY VPN software over the years, with the entire process being greatly simplified.
LogMeIn Hamachi is one of the better VPN clients I’ve seen. You can get up and running very quickly with almost no configuration needed. This product will let you connect to an entire network and share network drives. Free for non-commercial use.
RealVNC means Virtual Network Computing. It is remote control software which allows you to access a server computer from another one named viewer. The two computers do not even have to be the same type. VNC is freely and publicly available and is in widespread active use by millions throughout industry, academia and privately.
Thursday, October 21, 2010
New "Attack Page" Scam in Firefox and Chrome
F-Secure reported a new malware campaign takes advantage of the "malicious site" warnings commonly displayed by both Firefox and Chrome to trick unsuspecting users into downloading a rogue antivirus application
The attack happens when Web surfers visit a page offering "SecurityTool," a known malware application that purports to be antivirus software. On both Firefox and Chrome, a fake warning page then pops up that mimics the messages those browsers normally give users who visit suspect sites.
On Firefox, the warning alert is titled, "Reported Attack Page!" while on Chrome the page reads, "Warning: Visiting this site may harm your computer!" Both such warnings invite users to "Download Updates." Users who click the download button then end up with a file called "ff_secure_upd.exe" on Firefox or "chrome_secure_upd.exe" on Google's browser; either way, what they really get is the rogue antivirus file and an invitation to pay a license fee for supposed protection.
Firefox users with scripts enabled, in fact, don't even have to click the "Download Updates" button--rather, they'll just be prompted to click "OK" to download "Firefox secure updates." Clicking "Cancel" only results in a repeated warning that updates need to be downloaded, F-Secure reported.
In addition to the "scareware," a hidden iFrame that's also part of the attack loads a Phoenix exploit kit from a different site, the security researcher noted, thereby exposing users to further exploitation. This latest attack is very similar to one uncovered in July, through which SecurityTool used a similar technique purportedly prompting Firefox users to update their Adobe Flash Player. In that case, the attack presented users with a fake version of the Firefox "Just Updated" page, which is typically shown when users open the browser for the first time after an update is downloaded.
On the fake version, however, the message warned that Adobe Flash Player hadn't yet been updated, and it prompted the user to download a file that is in fact the rogue antivirus software, according to F-Secure. The new "Reported Attack Page!" alert, however, relies particularly heavily on Firefox users' uncertainty as to what genuine warning pages look like. In fact, such pages never request that users download updates; rather, they give the option of either leaving the site or overriding the block and continuing to load the page. F-Secure's blog post includes an authentic Firefox block page for users who want a reliable visual image.
Originally posted at Yahoo News
The attack happens when Web surfers visit a page offering "SecurityTool," a known malware application that purports to be antivirus software. On both Firefox and Chrome, a fake warning page then pops up that mimics the messages those browsers normally give users who visit suspect sites.
On Firefox, the warning alert is titled, "Reported Attack Page!" while on Chrome the page reads, "Warning: Visiting this site may harm your computer!" Both such warnings invite users to "Download Updates." Users who click the download button then end up with a file called "ff_secure_upd.exe" on Firefox or "chrome_secure_upd.exe" on Google's browser; either way, what they really get is the rogue antivirus file and an invitation to pay a license fee for supposed protection.
Firefox users with scripts enabled, in fact, don't even have to click the "Download Updates" button--rather, they'll just be prompted to click "OK" to download "Firefox secure updates." Clicking "Cancel" only results in a repeated warning that updates need to be downloaded, F-Secure reported.
In addition to the "scareware," a hidden iFrame that's also part of the attack loads a Phoenix exploit kit from a different site, the security researcher noted, thereby exposing users to further exploitation. This latest attack is very similar to one uncovered in July, through which SecurityTool used a similar technique purportedly prompting Firefox users to update their Adobe Flash Player. In that case, the attack presented users with a fake version of the Firefox "Just Updated" page, which is typically shown when users open the browser for the first time after an update is downloaded.
On the fake version, however, the message warned that Adobe Flash Player hadn't yet been updated, and it prompted the user to download a file that is in fact the rogue antivirus software, according to F-Secure. The new "Reported Attack Page!" alert, however, relies particularly heavily on Firefox users' uncertainty as to what genuine warning pages look like. In fact, such pages never request that users download updates; rather, they give the option of either leaving the site or overriding the block and continuing to load the page. F-Secure's blog post includes an authentic Firefox block page for users who want a reliable visual image.
Originally posted at Yahoo News
Tuesday, October 19, 2010
Clean up Your PC: Multiple Options
Your PC will slow down over time. Here's how to clean it up without having to reinstall Windows or reformat your hard drive.
You can, of course, manually clean out a lot of the junk on your system. Here are some ways to tackle the job.
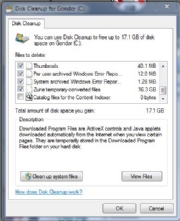
Disk Cleanup
The past few versions of Windows have shipped with the Disk Cleanup utility, which you can launch by clicking Start, All Programs, Accessories, System Tools, Disk Cleanup. When I used this tool on my machine, I discovered 16.3 gigabytes of Zune temporary converted files.
You can manually clean out old system files, as well--but that can be perilous, so delete such files with care. Also, Disk Cleanup allows you (under the More Options tab) to delete all but the most recent System Restore and Shadow Copy files. I recommend avoiding that--you never know if you'll need an older restore point to get a usable machine back if you run into problems.
Defrag Your Drive
Defragmenting your hard drive is useful after you've performed a sweep with Disk Cleanup. During the defrag process, your system performance will slow down, since the defragger keeps the hard drives pretty busy. The Windows 7 defrag utility is somewhat smart about this, but your PC will still be less responsive during the process; it's best to run the utility when you don't need timely system access.
Maintaining a Clean System: Steps to Take
Once you've cleaned out the junk, how do you keep your Windows system relatively clean? Here are several pointers. If an application has an "advanced" install option, use it. Go ahead and install to the default locations (if you want), but check what's being installed. Sometimes you'll have the option of telling the program not to run anything at system startup. Always watch the installer dialog box. Many users merely click the Next button every time the application's installer prompts them to do so.
But often the window will have checkboxes that install additional items, such as browser toolbars, quick-startup utilities, or other junk. If a window pops up in your browser asking you to install something, make sure you know what it is. It may just be a simple tool to help your browsing, or it may install something that runs at startup and saps your system resources. (Weatherbug, anyone?) In the worst-case scenario, it will install malware. Use tools such as Soluto and Msconfig frequently to make sure useless junk isn't running at startup. Clean your drive frequently, particularly temporary Internet and temporary installation files.
It takes only a few minutes a week to keep your system relatively clean, and if you do that, you'll likely be able to postpone the dreaded reformat and reinstall for a very long time.
You can, of course, manually clean out a lot of the junk on your system. Here are some ways to tackle the job.
Disk Cleanup
The past few versions of Windows have shipped with the Disk Cleanup utility, which you can launch by clicking Start, All Programs, Accessories, System Tools, Disk Cleanup. When I used this tool on my machine, I discovered 16.3 gigabytes of Zune temporary converted files.
You can manually clean out old system files, as well--but that can be perilous, so delete such files with care. Also, Disk Cleanup allows you (under the More Options tab) to delete all but the most recent System Restore and Shadow Copy files. I recommend avoiding that--you never know if you'll need an older restore point to get a usable machine back if you run into problems.
Defrag Your Drive
Defragmenting your hard drive is useful after you've performed a sweep with Disk Cleanup. During the defrag process, your system performance will slow down, since the defragger keeps the hard drives pretty busy. The Windows 7 defrag utility is somewhat smart about this, but your PC will still be less responsive during the process; it's best to run the utility when you don't need timely system access.
System Configuration Utility
This tool is more commonly referred to as Msconfig. You launch it by typing msconfig in the Run bar. Using Msconfig lets you manually specify services to run, as well as startup applications. It's far from perfect, however: It doesn't give you any advice as to what services can be safely disabled, though you can hide Windows services, which makes the Services tab a little more manageable The Startup tab is more useful. The caution here, though, is that if you disable everything willy-nilly, some of your applications (such as your antivirus software) may not work. Still, stuff like the QuickTime Helper app and the Adobe Acrobat helper can be safely disabled.
Registry Editor
Use the Windows Registry Editor, aka "regedit," with caution. You could easily delete keys from the Registry permanently, and render your system unusable. A less serious risk is that you could make applications unusable, and then have to reinstall them. I've run into situations, however, in which a partial Registry edit makes it impossible to uninstall or reinstall an application--but the app won't run. If you're going to edit the Registry yourself, back it up first.
This screenshot of the Registry Editor shows only the first-level view; on lower levels the typical Registry contains many thousands of entries, often with arcane names such as
HKEY_LOCAL_MACHINE\SOFTWARE\{9F5FBC24-EFE2-4f90-B498-EC0FB7D47D15}. Understanding what to delete and what to keep can be fraught with peril.
If you're trying to root out Registry entries for an incompletely uninstalled piece of software, the editor does allow you to search. If you do this, be very specific with the search string. The application name is much better than, say, the company name. Searching for "Zune," for instance, will likely yield much safer results than searching for "Microsoft."
If you're trying to root out Registry entries for an incompletely uninstalled piece of software, the editor does allow you to search. If you do this, be very specific with the search string. The application name is much better than, say, the company name. Searching for "Zune," for instance, will likely yield much safer results than searching for "Microsoft."
Maintaining a Clean System: Steps to Take
Once you've cleaned out the junk, how do you keep your Windows system relatively clean? Here are several pointers. If an application has an "advanced" install option, use it. Go ahead and install to the default locations (if you want), but check what's being installed. Sometimes you'll have the option of telling the program not to run anything at system startup. Always watch the installer dialog box. Many users merely click the Next button every time the application's installer prompts them to do so.
But often the window will have checkboxes that install additional items, such as browser toolbars, quick-startup utilities, or other junk. If a window pops up in your browser asking you to install something, make sure you know what it is. It may just be a simple tool to help your browsing, or it may install something that runs at startup and saps your system resources. (Weatherbug, anyone?) In the worst-case scenario, it will install malware. Use tools such as Soluto and Msconfig frequently to make sure useless junk isn't running at startup. Clean your drive frequently, particularly temporary Internet and temporary installation files.
It takes only a few minutes a week to keep your system relatively clean, and if you do that, you'll likely be able to postpone the dreaded reformat and reinstall for a very long time.
Labels:
pc performance,
pc tips,
slow pc
Friday, October 15, 2010
Why Windows OS gets Slower in Time
Windows slowdown has three main causes: The Windows Registry gets bigger, DLLs and other junk are needlessly duplicated, and hard drives become fragmented. One other cause on machines that have a lot of programs installed is that a lot of background services and applications can be running, without your knowledge.
These potential problems aren't mutually exclusive.
The Registry can swell as you install more software, which in turn loads a lot of background tasks. Plus, your hard drive may fill up, making Windows auto-defragging harder. But let's look at these issues one at a time.
The Windows Registry
Windows maintains configuration settings, application install settings, and options in a database called the Windows Registry. As you install and uninstall applications or make changes to Windows, the Registry tends to grow larger and larger. For example, the Registry on my production PC, which has a ton of apps installed, is about 384MB--and that's just a backup.
As the Registry expands, applications and services that use it take longer to load. Searches conducted through the Registry by apps that may have written their data in multiple places also start to require more time. Some applications, such as security tools and certain media players (PowerDVD and the like), touch the data in a large number of locations.
The other culprit behind Registry bloat is incomplete uninstalls. Most users install or uninstall only a few applications per year, but some people (gamers and power users come to mind) tend to install and remove many programs. Incomplete uninstalls leave residue in the Registry, which adds to its size. Windows 7 and its program uninstaller is much improved in this respect, but still not perfect. As it turns out, however, Registry cleaners aren't really the way to go.
Associated Application Crud
When you install applications, sometimes they need various runtime modules to run. See all those separately installed copies of the Microsoft Visual C++ redistributable? You really need only the latest version. If you're running the 64-bit version, you might need two copies, one for 32-bit (labeled "x86") and one for 64-bit (x64). This is just one example of the kind of junk that can get installed on a system. It's hard to stop and track down, and determining whether removing it might break something is often difficult.
Unneeded Background Services and Tasks
The more stuff you install, the more the programs seem to install some kind of service in the background. Maybe that service will speed up an application launch. Maybe it's a control-panel applet for a high-end gaming mouse. Do I really need Impulse Now running all the time? I use it only when I'm running a game downloaded from Stardock's Impulse digital-delivery system, or when I'm buying a game from there. I certainly don't need it. And I rarely use Microsoft OneNote, so that doesn't have to run either.
Hard-Drive Issues
A machine's file system will become fragmented eventually. Windows 7 tries to minimize that by running the defragger in the background when the PC is idle. But if you frequently create and delete files (or use applications that create and delete files regularly), the file system is bound to become fragmented. System-performance issues can also crop up if the drive gets too full. If a drive is more than 90 percent full, swapping from main memory to the drive becomes very slow, which can drag down the system as a whole. It may be time to clean out your drive--or buy a bigger one.
Incomplete Uninstalls
The Windows uninstaller--as well as similar uninstall apps that ship with some software--doesn't always completely remove an application. This shortcoming causes the Registry to balloon, leaves extraneous files on the hard drive, and otherwise cruds up a system.
The Registry can swell as you install more software, which in turn loads a lot of background tasks. Plus, your hard drive may fill up, making Windows auto-defragging harder. But let's look at these issues one at a time.
The Windows Registry
Windows maintains configuration settings, application install settings, and options in a database called the Windows Registry. As you install and uninstall applications or make changes to Windows, the Registry tends to grow larger and larger. For example, the Registry on my production PC, which has a ton of apps installed, is about 384MB--and that's just a backup.
As the Registry expands, applications and services that use it take longer to load. Searches conducted through the Registry by apps that may have written their data in multiple places also start to require more time. Some applications, such as security tools and certain media players (PowerDVD and the like), touch the data in a large number of locations.
The other culprit behind Registry bloat is incomplete uninstalls. Most users install or uninstall only a few applications per year, but some people (gamers and power users come to mind) tend to install and remove many programs. Incomplete uninstalls leave residue in the Registry, which adds to its size. Windows 7 and its program uninstaller is much improved in this respect, but still not perfect. As it turns out, however, Registry cleaners aren't really the way to go.
Associated Application Crud
When you install applications, sometimes they need various runtime modules to run. See all those separately installed copies of the Microsoft Visual C++ redistributable? You really need only the latest version. If you're running the 64-bit version, you might need two copies, one for 32-bit (labeled "x86") and one for 64-bit (x64). This is just one example of the kind of junk that can get installed on a system. It's hard to stop and track down, and determining whether removing it might break something is often difficult.
Unneeded Background Services and Tasks
The more stuff you install, the more the programs seem to install some kind of service in the background. Maybe that service will speed up an application launch. Maybe it's a control-panel applet for a high-end gaming mouse. Do I really need Impulse Now running all the time? I use it only when I'm running a game downloaded from Stardock's Impulse digital-delivery system, or when I'm buying a game from there. I certainly don't need it. And I rarely use Microsoft OneNote, so that doesn't have to run either.
Hard-Drive Issues
A machine's file system will become fragmented eventually. Windows 7 tries to minimize that by running the defragger in the background when the PC is idle. But if you frequently create and delete files (or use applications that create and delete files regularly), the file system is bound to become fragmented. System-performance issues can also crop up if the drive gets too full. If a drive is more than 90 percent full, swapping from main memory to the drive becomes very slow, which can drag down the system as a whole. It may be time to clean out your drive--or buy a bigger one.
Incomplete Uninstalls
The Windows uninstaller--as well as similar uninstall apps that ship with some software--doesn't always completely remove an application. This shortcoming causes the Registry to balloon, leaves extraneous files on the hard drive, and otherwise cruds up a system.
Labels:
fix registry,
pc tips,
slow pc
Tuesday, October 12, 2010
Fix Random Windows 7 Freezes, Test Mode
Learn how to stop Windows 7 from freezing at will, remove a mysterious "test mode" watermark, and find out exactly what version of Windows you're running.
Of all the hassles that can plague a PC user (and, trust me, there are many), few are as infuriating as random lockups. There you are, typing along, when suddenly everything just freezes. No error message, no blue screen, just a locked-up, unresponsive system. I've been there. I feel your pain.
If you're a Windows 7 (or Windows Server 2008 R2) user, you may be in luck: Microsoft recently issued a hotfix for systems that stop responding randomly.
What causes the problem? Microsoft says it's "a deadlock condition between the Lsass.exe process, the Redirected Drive Buffering Subsystem (Rdbss.sys) driver, and the Winsock kernel." Well, duh! That was going to be my first guess.
The hotfix is available for both 32- and 64-bit versions of Windows 7. (Fun fact: you'll often see these versions represented as "x86" and "x64," respectively.) To get it, go to the appropriate Microsoft Support page, click "View and request hotfix downloads," accept Microsoft's terms, choose the hotfix compatible with your system, and provide your e-mail address. Click "Request hotfix," then check your e-mail inbox for a message containing a link to the download.
I'm not sure why Microsoft makes you jump through these hoops, but, then again, I'm not sure why Microsoft does half the things it does.
Remove the 'Test Mode' Watermark from Windows 7
Isn't it cute the way Windows always finds new ways to surprise and annoy you? Like today, for instance, I booted my system and noticed something new in the lower right corner:
Test Mode
Windows 7
Build 7600
I've been using this licensed and activated version of Windows 7 for nearly a year. What's with the bizarro watermark all of a sudden?
Who knows? I've also been trying to troubleshoot a weird, out-of-the-blue "security warning" message that appears whenever I click a Start Menu program. As I regularly tell my dad when crazy stuff like this happens: "That's Windows for you."
Don't get me wrong--I like Windows 7 a lot. I'm just a little fed up with this kind of thing. And I recently gave up coffee, so I'm a little cranky. Anyway, if you've encountered that same watermark in Windows 7, here's how to get rid of it:
Oh, Windows--what exciting surprises do you have in store for me tomorrow?
Quickly Determine Which Version of Windows You Have
You probably know if your PC is running Windows XP, Vista, or 7--but do you know which version of Windows it is? For example, is it XP Home? Windows 7 Ultimate? And is it the 32-bit or 64-bit variety?
Knowing the answer to the last question is increasingly important these days, as you can't run 64-bit software on a 32-bit OS. Likewise, if you do have 64-bit Windows (often referred to as "x64"), you should always opt for 64-bit versions of your favorite applications (when available).
Windows doesn't paste this information anywhere in plain sight, but it's easy enough to find. In Vista and 7, right-click your Computer icon and choose Properties. Presto: all the information you need in one handy box. You can also click the Start button, type version, and then click Show which operating system your computer is running.
Of all the hassles that can plague a PC user (and, trust me, there are many), few are as infuriating as random lockups. There you are, typing along, when suddenly everything just freezes. No error message, no blue screen, just a locked-up, unresponsive system. I've been there. I feel your pain.
If you're a Windows 7 (or Windows Server 2008 R2) user, you may be in luck: Microsoft recently issued a hotfix for systems that stop responding randomly.
What causes the problem? Microsoft says it's "a deadlock condition between the Lsass.exe process, the Redirected Drive Buffering Subsystem (Rdbss.sys) driver, and the Winsock kernel." Well, duh! That was going to be my first guess.
The hotfix is available for both 32- and 64-bit versions of Windows 7. (Fun fact: you'll often see these versions represented as "x86" and "x64," respectively.) To get it, go to the appropriate Microsoft Support page, click "View and request hotfix downloads," accept Microsoft's terms, choose the hotfix compatible with your system, and provide your e-mail address. Click "Request hotfix," then check your e-mail inbox for a message containing a link to the download.
I'm not sure why Microsoft makes you jump through these hoops, but, then again, I'm not sure why Microsoft does half the things it does.
Remove the 'Test Mode' Watermark from Windows 7
Isn't it cute the way Windows always finds new ways to surprise and annoy you? Like today, for instance, I booted my system and noticed something new in the lower right corner:
Test Mode
Windows 7
Build 7600
I've been using this licensed and activated version of Windows 7 for nearly a year. What's with the bizarro watermark all of a sudden?
Who knows? I've also been trying to troubleshoot a weird, out-of-the-blue "security warning" message that appears whenever I click a Start Menu program. As I regularly tell my dad when crazy stuff like this happens: "That's Windows for you."
Don't get me wrong--I like Windows 7 a lot. I'm just a little fed up with this kind of thing. And I recently gave up coffee, so I'm a little cranky. Anyway, if you've encountered that same watermark in Windows 7, here's how to get rid of it:
- Click Start and type cmd.
- Right-click cmd and choose Run as Administrator.
- At the command prompt that appears, type bcdedit.exe -set loadoptions ENABLE_INTEGRITY_CHECKS
- Press Enter, then type bcdedit.exe -set TESTSIGNING OFF
- Press Enter, then type exit and press Enter one last time.
- Reboot your PC.
- That should send the watermark packing; it did on my system.
Oh, Windows--what exciting surprises do you have in store for me tomorrow?
Quickly Determine Which Version of Windows You Have
You probably know if your PC is running Windows XP, Vista, or 7--but do you know which version of Windows it is? For example, is it XP Home? Windows 7 Ultimate? And is it the 32-bit or 64-bit variety?
Knowing the answer to the last question is increasingly important these days, as you can't run 64-bit software on a 32-bit OS. Likewise, if you do have 64-bit Windows (often referred to as "x64"), you should always opt for 64-bit versions of your favorite applications (when available).
Windows doesn't paste this information anywhere in plain sight, but it's easy enough to find. In Vista and 7, right-click your Computer icon and choose Properties. Presto: all the information you need in one handy box. You can also click the Start button, type version, and then click Show which operating system your computer is running.
Labels:
software tips,
windows 7
Major Microsoft Patches
Microsoft said it will deliver a record 16 security updates next week to patch a whopping 49 vulnerabilities in Windows, Internet Explorer (IE), Office and SharePoint.
Andrew Storms, director of security operations for nCircle Security, called the massive update "daunting, again."
Four of the 16 updates were tagged with Microsoft's "critical" label, the highest threat ranking in its four-step scoring system. Another 10 were marked "important," the second-highest rating, while the remaining pair were labeled as "moderate."
Nine of the updates could be exploited by attackers to inject malicious code into vulnerable PCs, Microsoft said in its usual bare-bones advance notification of the updates scheduled for release October 12. Microsoft often labels remote code executable bugs -- the most dangerous -- as important when the vulnerable components are not switched on by default or when other mitigating factors, such as defensive measures like ASLR and DEP, may protect some users.
Nine of Tuesday's Windows updates will apply to Windows 7 -- including all three of those marked critical -- while Windows Server 2008 R2 will also receive nine updates, two of them critical. While Microsoft has touted Windows 7 as its most-secure OS ever, and wants Windows XP users to ditch the nine-year-old software for the new edition, fewer of next week's updates apply to the aged operating system than to Windows 7. XP will be affected by eight of the 13 bulletins, and just two of the three pegged as critical. The critical IE update will affect IE6, IE7 and IE8. Microsoft did not reply to questions about whether it will also update IE9, which was released as a beta three weeks ago.
Originally posted at PCWorld
Four of the 16 updates were tagged with Microsoft's "critical" label, the highest threat ranking in its four-step scoring system. Another 10 were marked "important," the second-highest rating, while the remaining pair were labeled as "moderate."
Nine of the updates could be exploited by attackers to inject malicious code into vulnerable PCs, Microsoft said in its usual bare-bones advance notification of the updates scheduled for release October 12. Microsoft often labels remote code executable bugs -- the most dangerous -- as important when the vulnerable components are not switched on by default or when other mitigating factors, such as defensive measures like ASLR and DEP, may protect some users.
Nine of Tuesday's Windows updates will apply to Windows 7 -- including all three of those marked critical -- while Windows Server 2008 R2 will also receive nine updates, two of them critical. While Microsoft has touted Windows 7 as its most-secure OS ever, and wants Windows XP users to ditch the nine-year-old software for the new edition, fewer of next week's updates apply to the aged operating system than to Windows 7. XP will be affected by eight of the 13 bulletins, and just two of the three pegged as critical. The critical IE update will affect IE6, IE7 and IE8. Microsoft did not reply to questions about whether it will also update IE9, which was released as a beta three weeks ago.
Originally posted at PCWorld
Saturday, October 9, 2010
Tweet Traffic Rush
You might have noticed that Twitter is the biggest news on
the internet now. With some hundreds of thousands of new
people joining Twitter each day, it is emerging as one of the
largest and fastest growing social networking sites at this time.
As there are millions of people joining up to and logging
into Twitter everyday, Twitter turns out a bigger and better
opportunity to get you loads of targeted traffic to your website.
Though you can access millions of people on Twitter, you will
need to work aptly in reaching out to them correctly. Here is
where Tweet Traffic Rush can help you out.
Tweet Traffic Rush is the easiest, fastest and most efficient
way to get a flood of laser targeted visitors to your site
through Twitter and this is... Absolutely FREE!
With Tweet Traffic Rush, you will be able to use Twitter to
spread your marketing messages virally and work in creating
an Avalanche of FREE Targeted Traffic to Your Website in a
very short time.
And how it works?
All you do is sign up for a free account. Then you will need to
add your twitter username in an appropriate category so as to
get a tiny piece of widget code. And once you add this widget
code to your websites, blogs or social networking sites, you'll
start getting more targeted visitors to your site.
If you are tired of and feel difficulty in spreading your marketing
messages across the net, TweetTrafficRush.com can get you
thousands of visitors to your site on autopilot.
Click on the Link and Create Your FREE Account NOW!! Tweet Traffic Rush
the internet now. With some hundreds of thousands of new
people joining Twitter each day, it is emerging as one of the
largest and fastest growing social networking sites at this time.
As there are millions of people joining up to and logging
into Twitter everyday, Twitter turns out a bigger and better
opportunity to get you loads of targeted traffic to your website.
Though you can access millions of people on Twitter, you will
need to work aptly in reaching out to them correctly. Here is
where Tweet Traffic Rush can help you out.
Tweet Traffic Rush is the easiest, fastest and most efficient
way to get a flood of laser targeted visitors to your site
through Twitter and this is... Absolutely FREE!
With Tweet Traffic Rush, you will be able to use Twitter to
spread your marketing messages virally and work in creating
an Avalanche of FREE Targeted Traffic to Your Website in a
very short time.
And how it works?
All you do is sign up for a free account. Then you will need to
add your twitter username in an appropriate category so as to
get a tiny piece of widget code. And once you add this widget
code to your websites, blogs or social networking sites, you'll
start getting more targeted visitors to your site.
If you are tired of and feel difficulty in spreading your marketing
messages across the net, TweetTrafficRush.com can get you
thousands of visitors to your site on autopilot.
Click on the Link and Create Your FREE Account NOW!! Tweet Traffic Rush

Labels:
Tweet,
Tweet Traffic Rush,
Twitter
Friday, October 1, 2010
EEye Digital launches Zero Day Tracker site
Until a patch is released, a security hole--known as a zero-day vulnerability--in effect makes your computer a sitting duck for anyone who writes an exploit for it and bothers to distribute it via e-mails and drive-by downloads on Web sites.
EEye Digital Security launched a Web site yesterday that lists current zero-day vulnerabilities and offers an archive on ones that have been patched. The Zero Day Tracker compiles information on publicly disclosed security holes and provides details on them including what software they affect, how severe they are, the potential impact and suggestions for workarounds and other protection techniques.
Marc Maiffret, co-founder and chief technology officer of eEye, describes the free site as a "one-stop shop" for zero-day information. "For the longest time the only company that would notify you about zero-days was Microsoft, and recently Adobe has started doing that," he said. "But there are still many other companies that have zero-day vulnerabilities that go unreported."
EEye Digital Security launched a Web site yesterday that lists current zero-day vulnerabilities and offers an archive on ones that have been patched. The Zero Day Tracker compiles information on publicly disclosed security holes and provides details on them including what software they affect, how severe they are, the potential impact and suggestions for workarounds and other protection techniques.
Marc Maiffret, co-founder and chief technology officer of eEye, describes the free site as a "one-stop shop" for zero-day information. "For the longest time the only company that would notify you about zero-days was Microsoft, and recently Adobe has started doing that," he said. "But there are still many other companies that have zero-day vulnerabilities that go unreported."
How good is Microsoft's free antivirus software?
Microsoft has officially unveiled its long-awaited consumer antivirus offering. Formerly code-named “Morro,” it’s now been christened Microsoft Security Essentials, and it will enter public beta testing next week. If you have a licensed copy of Windows XP (Service Pack 2 or above), Windows Vista, or Windows 7, you’ll be able to download and install the software at no additional charge. No subscription is required for ongoing definition updates, either. The final release is scheduled for this fall.
The public beta will be limited to 75,000 downloads, Microsoft says, and the targets are global. The initial beta release is limited to the United States, Israel (where a core development team is based), and Brazil. Next month, the beta will open up for users in China. It’s no coincidence that Microsoft is rolling out early in Brazil and China, which are large-scale vectors of malware infections because of the sheer number of Windows users running without antivirus protection. According to Microsoft, barriers to adoption of paid security software are especially high in developing markets, where internet access is slower and credit cards are unavailable to a large percentage of the population.
Microsoft Security Essentials requires validation, which means it won’t be available to anyone using a pirated copy of Windows. But it won’t require registration or personal information of any kind. In an interview last week, Theresa Burch, director of product management for Microsoft Security Essentials, confirmed that decision in no uncertain terms: “We collect no information from you at all,” she told me. No Windows Live ID, nothing. You agree to the EULA, validate, download, and you’re done.”
Originally posted on ZDNet
The public beta will be limited to 75,000 downloads, Microsoft says, and the targets are global. The initial beta release is limited to the United States, Israel (where a core development team is based), and Brazil. Next month, the beta will open up for users in China. It’s no coincidence that Microsoft is rolling out early in Brazil and China, which are large-scale vectors of malware infections because of the sheer number of Windows users running without antivirus protection. According to Microsoft, barriers to adoption of paid security software are especially high in developing markets, where internet access is slower and credit cards are unavailable to a large percentage of the population.
Microsoft Security Essentials requires validation, which means it won’t be available to anyone using a pirated copy of Windows. But it won’t require registration or personal information of any kind. In an interview last week, Theresa Burch, director of product management for Microsoft Security Essentials, confirmed that decision in no uncertain terms: “We collect no information from you at all,” she told me. No Windows Live ID, nothing. You agree to the EULA, validate, download, and you’re done.”
Originally posted on ZDNet
Tuesday, September 21, 2010
Increasing Your Computer’s Performance the Easy Way
 Increasing Your Computer’s Performance the Easy Way
Increasing Your Computer’s Performance the Easy WayFor Windows Vista/2007 and XP, Includes: PDF ebook.
System optimization and tweaks for Windows Vista/XP. Would you like your computer to run as fast as it did the very first day you brought it home? I uploaded an easy to follow step by step tutorial that will get your computer running great again. Through out this tutorial you will learn basic system maintenance tasks, how to clean and edit your windows registry, boost internet explorer’s performance, and optimize your system. If at any time you feel these tasks are too difficult or time consuming then download a Free copy of Increasing Your Computer’s Performance the Easy Way
Labels:
ebook,
pc performance,
pc tips
Microsoft Windows Performance Boost
 Microsoft Windows Performance Boost
Microsoft Windows Performance BoostThis Product Includes: PDF ebook.
Is my System Past its Prime?? When your computer was brand new it was running at its peek performance. There was no waiting when you clicked on an icon or visited a web page. There were no pop ups or mysterious errors slowing you down. Now those days are gone and you may be thinking your computer is past its prime, out of date or just plain broken. I have been working on computers for 20 years and I will tell you rarely is hardware ever the problem. In fact I will put a well maintained older system against a newer poorly maintained system any day of the week. What does this mean? Repairing your version of Windows and learning simple maintenance steps will save you from spending hundreds of dollars on a new computer. I find most people would rather give up and buy a new computer then learn how to repair and maintain the one they already own. Hey I understand lazy we all get that way when it comes to learning new things. That’s why I have tried by best to make this book as simple and easy to follow as possible.
To read more download Microsoft Windows Performance Boost PDF FREE
Labels:
ebook,
pc performance,
pc tips
Thursday, September 16, 2010
Ika-tako Virus Replaces Your Files With Octopus Photos
It’s always frustrating to find that your computer has been infected with a virus, especially one that can potentially wipe your files. However one hacker decided that he would bring a little humor to viruses by replacing any infected file with a particularly cute sea creature anime.
The Ika-tako virus (which is Japanese for Squid-Octopus) as it has been named first came to shore in May via Japanese file sharing Website Winny.
Since then, it has reportedly gone on to infect somewhere between 20,000 and 50,000 computers, according to Asahi.com. The virus disguises itself in music files, which users then download. Once the file is played, the malware runs through the computer’s hard drive, infecting anything from family photos to important OS files. The infected files are swapped with the squid, octopus or sea urchin pictures and removed, then supposedly sent to the hacker's server.
The good news is that the hacker, Masato Nakatsuji, was found and arrested. It’s not the first time this guy has been arrested for malware creation either--he was convicted for crafting a similar virus back in 2008, but had used images from the copyrighted anime cartoon Clannad.
He reportedly told police this time that he wanted to see “how much my computer programming skills had improved since the last time I was arrested.” This time, he was arrested on the grounds of property destruction, a first for police in Tokyo. At least he handmade the images himself this time I guess.
Unfortunately there is no known fix for the virus just yet, so bad news for those already infected, unless police can get into the server he set up. However, considering he had thousands of people’s information stored on the server, it shouts to me that there was a bigger motive behind this virus that just practicing his computer skills.
Originally posted at PCWorld
Since then, it has reportedly gone on to infect somewhere between 20,000 and 50,000 computers, according to Asahi.com. The virus disguises itself in music files, which users then download. Once the file is played, the malware runs through the computer’s hard drive, infecting anything from family photos to important OS files. The infected files are swapped with the squid, octopus or sea urchin pictures and removed, then supposedly sent to the hacker's server.
The good news is that the hacker, Masato Nakatsuji, was found and arrested. It’s not the first time this guy has been arrested for malware creation either--he was convicted for crafting a similar virus back in 2008, but had used images from the copyrighted anime cartoon Clannad.
He reportedly told police this time that he wanted to see “how much my computer programming skills had improved since the last time I was arrested.” This time, he was arrested on the grounds of property destruction, a first for police in Tokyo. At least he handmade the images himself this time I guess.
Unfortunately there is no known fix for the virus just yet, so bad news for those already infected, unless police can get into the server he set up. However, considering he had thousands of people’s information stored on the server, it shouts to me that there was a bigger motive behind this virus that just practicing his computer skills.
Originally posted at PCWorld
Trojan Monitors Your Porn Surfing Habits
In an era where online privacy seems like an oxymoron, is it so bad to have your browsing history publicly available? Or to pay less than $20 to have these details removed from the Internet?
Several Trojan horses spreading around the Internet these days spam your entire address book with bogus messages and attempt to delete your computer’s security software.
But the Kenzero Trojan out of Japan goes further than pretending to be a legitimate program: Hackers behind the program not only post your browser history, favorites, illegally-downloaded porn, and clipboard content to a public Website, they demand payment of about $18 to remove the personal details of your browsing history.
Kenzero is a Trojan of the “ransomware” variety, where a malicious program masquerading as a game registration window takes your personal details then attempts to extort money out of you. The Trojan then posts that you’ve been downloading illegal Hentai (explicit anime) games, and that instead of just being out $20, you’ll find that scammers have sold your credit card information to the highest bidder. How does Kenzero spread? Mostly via the Winny file-sharing network, which has approximately 200 million users).
Though if you’re illegaling downloading computer games, why would you give personal details to a pirated piece of software? It's food for thought. While you’re mulling that, there’s even a paper [PDF] on similar Japanese scams being presented at the upcoming Association for Computing Machinery Computer and Communications Security conference.
Originally posted at PCWorld
But the Kenzero Trojan out of Japan goes further than pretending to be a legitimate program: Hackers behind the program not only post your browser history, favorites, illegally-downloaded porn, and clipboard content to a public Website, they demand payment of about $18 to remove the personal details of your browsing history.
Kenzero is a Trojan of the “ransomware” variety, where a malicious program masquerading as a game registration window takes your personal details then attempts to extort money out of you. The Trojan then posts that you’ve been downloading illegal Hentai (explicit anime) games, and that instead of just being out $20, you’ll find that scammers have sold your credit card information to the highest bidder. How does Kenzero spread? Mostly via the Winny file-sharing network, which has approximately 200 million users).
Though if you’re illegaling downloading computer games, why would you give personal details to a pirated piece of software? It's food for thought. While you’re mulling that, there’s even a paper [PDF] on similar Japanese scams being presented at the upcoming Association for Computing Machinery Computer and Communications Security conference.
Originally posted at PCWorld
Tuesday, September 14, 2010
zero-day hole in Flash Player
Adobe Systems on Monday warned of a zero-day hole in Flash Player that reportedly is being exploited in the wild and could allow an attacker to take control of a computer.
The critical vulnerability affects Adobe Flash Player 10.1.82.76 and earlier versions for Windows, Mac, Linux, Solaris, and Android. It also affects Adobe Reader 9.3.4 and earlier version for Windows, Mac, and Unix and Adobe Acrobat 9.3.4 and earlier versions for Windows and Mac. Adobe is not aware of any attacks exploiting the hole against Adobe Reader or Acrobat, the company said in its security advisory.
Adobe is finalizing a fix for the hole and expects to provide an update for Flash Player for Windows, Mac, Solaris, and Android during the week of September 27, the advisory said. Updates for Adobe Reader are expected during the week of October 4. Adobe is moving up the date of its next quarterly security update for Adobe Reader and Acrobat and will also release a patch the week of October 4 for a critical zero-day hole in Adobe Reader and Acrobat that was disclosed last week and is being exploited in attacks on. As a result, there will be no updates on October 12, which was the next scheduled quarterly release date. In the meantime, Microsoft has a tool that can help block the attacks on Adobe Reader and Acrobat on Windows machines. Read more:
The critical vulnerability affects Adobe Flash Player 10.1.82.76 and earlier versions for Windows, Mac, Linux, Solaris, and Android. It also affects Adobe Reader 9.3.4 and earlier version for Windows, Mac, and Unix and Adobe Acrobat 9.3.4 and earlier versions for Windows and Mac. Adobe is not aware of any attacks exploiting the hole against Adobe Reader or Acrobat, the company said in its security advisory.
Adobe is finalizing a fix for the hole and expects to provide an update for Flash Player for Windows, Mac, Solaris, and Android during the week of September 27, the advisory said. Updates for Adobe Reader are expected during the week of October 4. Adobe is moving up the date of its next quarterly security update for Adobe Reader and Acrobat and will also release a patch the week of October 4 for a critical zero-day hole in Adobe Reader and Acrobat that was disclosed last week and is being exploited in attacks on. As a result, there will be no updates on October 12, which was the next scheduled quarterly release date. In the meantime, Microsoft has a tool that can help block the attacks on Adobe Reader and Acrobat on Windows machines. Read more:
Searching for free stuff online can be costly
It's common knowledge that you can catch computer viruses on porn Web sites. But did you know it's also risky to surf the Web searching for free movies or music?
A study from McAfee to be released on Tuesday finds that adding the word "free" when looking for entertainment content in search engines greatly increases the chances of landing on a site hosting malware. For instance, searching for free music ringtones increases the chances of hitting a malicious site by 300 percent, according to the report, "Digital Music & Movies Report: The True Cost of Free Entertainment." (PDF) Searching for "lyrics" for a particular artist is twice as risky on average as searching for "ringtones" for the same artist for the first five pages of results, the report found. And including the term "MP3" increases the riskiness of music searches in general.
There has been a 40 percent increase in the number of Web sites that are delivering infected MP3 files or that seem to be built for purposes of financial fraud or delivering malware, according to the report. Meanwhile, McAfee found malware associated with a number of Web sites around the world advertising free downloads of sports games, movies, and TV shows. Twelve percent of sites that distribute unauthorized content are distributing malware, and 7 percent of sites offering unauthorized content have associations with cybercrime organizations, the report concluded. "The sites often look very professional and attempt to lure the user with the idea of a 'trial period' or even some nominal fee that is much less than what may ultimately be charged," the report says. "Once the user agrees, they have to authorize their computer to access and interact with computers that are involved in a wide range of schemes--from money laundering to stealing credentials such as user names and passwords. In addition, with this access, your computer is profiled--with all of its software versions, user agents, and any other date--and this information can be provided to third parties for malicious purposes. (This is often called 'fingerprinting.')"
To reduce the chances of landing on malicious sites, McAfee recommends avoiding the use of the word "free" in searches for entertainment content, avoiding clicking on links in banner ads on content sites that aren't well established, not clicking on links posted in forums and on fan pages, keeping security software up to date, and using safe search plug-ins like McAfee Site Advisor that warns of potentially risky sites. Read more:
A study from McAfee to be released on Tuesday finds that adding the word "free" when looking for entertainment content in search engines greatly increases the chances of landing on a site hosting malware. For instance, searching for free music ringtones increases the chances of hitting a malicious site by 300 percent, according to the report, "Digital Music & Movies Report: The True Cost of Free Entertainment." (PDF) Searching for "lyrics" for a particular artist is twice as risky on average as searching for "ringtones" for the same artist for the first five pages of results, the report found. And including the term "MP3" increases the riskiness of music searches in general.
There has been a 40 percent increase in the number of Web sites that are delivering infected MP3 files or that seem to be built for purposes of financial fraud or delivering malware, according to the report. Meanwhile, McAfee found malware associated with a number of Web sites around the world advertising free downloads of sports games, movies, and TV shows. Twelve percent of sites that distribute unauthorized content are distributing malware, and 7 percent of sites offering unauthorized content have associations with cybercrime organizations, the report concluded. "The sites often look very professional and attempt to lure the user with the idea of a 'trial period' or even some nominal fee that is much less than what may ultimately be charged," the report says. "Once the user agrees, they have to authorize their computer to access and interact with computers that are involved in a wide range of schemes--from money laundering to stealing credentials such as user names and passwords. In addition, with this access, your computer is profiled--with all of its software versions, user agents, and any other date--and this information can be provided to third parties for malicious purposes. (This is often called 'fingerprinting.')"
To reduce the chances of landing on malicious sites, McAfee recommends avoiding the use of the word "free" in searches for entertainment content, avoiding clicking on links in banner ads on content sites that aren't well established, not clicking on links posted in forums and on fan pages, keeping security software up to date, and using safe search plug-ins like McAfee Site Advisor that warns of potentially risky sites. Read more:
Labels:
network scanner,
Tech News
Saturday, September 11, 2010
"Here You Have" worm is a Windows Problem
Every time a virus like the current "Here You Have" worm comes around, people shake their heads, wring their hands and wonder how "computer security" can be improved.
The assumption, for many, is that malware like this is simply part of having a computer. Thank goodness for the PC security industry, working hard to protect us with expensive software! The fact, however, is that malware like this does not go hand-in-hand with having a networked computer--it goes hand-in-hand with Windows. Microsoft Windows is the reason our culture gets threatened again and again by malware; if the world ran Linux instead, it wouldn't be a problem. Here's why.
1. Users Are Dumb
There's no point denying it -- humans are extremely gullible, forgetful, distracted, and yes, just plain stupid sometimes. That is simply a fact of life, and no "helpful reminders" or even automated warning systems are going to keep them from being stupid. Offer them pictures of cute puppies or porn, and they'll go wherever you want them to.
This is only a problem, however, because of Windows. Rather than protecting foolish users from themselves by minimizing the potential consequences--which is what a good operating system should do--Windows gives them all administrator access by default. That means that they pretty much have the keys to the castle at all times--which, in turn, means that viruses do too.
As I've said before, it's like giving terrorists high-level government positions. With Linux, on the other hand, users do not have "root" privileges by default. So, even if a Linux system is compromised--which is rare--the virus won't have the access it would need to do damage systemwide; rather, just the user's local files and programs would typically be affected. That's much less motivating for evil-doers.
2. It's a Monoculture
So Windows gives each and every user the keys to his or her local castle, which--thanks to the Internet--is linked to every other castle on the planet. Since the majority of those also run Windows, imagine the fun viruses can--and do--have! It's a simple matter of frolicking from one castle to another--again and again and again--taking the keys, and then watching the email servers fall! It's a worm's dream come true.
That, of course, is why Linux isn't popular with worm developers. With the diversity of environments that Linux includes--Ubuntu, Debian, Fedora, and so on, not to mention all the many shells, packaging systems, mail clients and even underlying architectures-- reaching more than a relatively small part of the Linux community is much more difficult. Much less gratifying for worms.
3. Closed Access
Less applicable in the present case, and yet still a factor in Windows' relative insecurity, is the fact that its code is closely guarded by Microsoft. No matter how many developers Redmond has, it simply can't compare with the countless users around the globe constantly scrutinizing Linux's open code for vulnerabilities. Microsoft developers also don't typically tell anyone about the problems they've found until a solution has been created, leaving the door open to exploits until that happens.
I'm certainly not saying that Linux is perfect, and any business user, in particular, should still enable firewalls, minimize the use of root privileges, and keep the system up to date. They could even implement a virus scanner for Linux, such as ClamAV.
The difference, though, is that such extra measures are not simply an accepted part of computing in the Linux world--they're additional steps you can take, if you want extra peace of mind. Malware is primarily a Windows problem. Use Linux, and you can mostly forget all about it.
Originally posted at Yahoo News
The assumption, for many, is that malware like this is simply part of having a computer. Thank goodness for the PC security industry, working hard to protect us with expensive software! The fact, however, is that malware like this does not go hand-in-hand with having a networked computer--it goes hand-in-hand with Windows. Microsoft Windows is the reason our culture gets threatened again and again by malware; if the world ran Linux instead, it wouldn't be a problem. Here's why.
1. Users Are Dumb
There's no point denying it -- humans are extremely gullible, forgetful, distracted, and yes, just plain stupid sometimes. That is simply a fact of life, and no "helpful reminders" or even automated warning systems are going to keep them from being stupid. Offer them pictures of cute puppies or porn, and they'll go wherever you want them to.
This is only a problem, however, because of Windows. Rather than protecting foolish users from themselves by minimizing the potential consequences--which is what a good operating system should do--Windows gives them all administrator access by default. That means that they pretty much have the keys to the castle at all times--which, in turn, means that viruses do too.
As I've said before, it's like giving terrorists high-level government positions. With Linux, on the other hand, users do not have "root" privileges by default. So, even if a Linux system is compromised--which is rare--the virus won't have the access it would need to do damage systemwide; rather, just the user's local files and programs would typically be affected. That's much less motivating for evil-doers.
2. It's a Monoculture
So Windows gives each and every user the keys to his or her local castle, which--thanks to the Internet--is linked to every other castle on the planet. Since the majority of those also run Windows, imagine the fun viruses can--and do--have! It's a simple matter of frolicking from one castle to another--again and again and again--taking the keys, and then watching the email servers fall! It's a worm's dream come true.
That, of course, is why Linux isn't popular with worm developers. With the diversity of environments that Linux includes--Ubuntu, Debian, Fedora, and so on, not to mention all the many shells, packaging systems, mail clients and even underlying architectures-- reaching more than a relatively small part of the Linux community is much more difficult. Much less gratifying for worms.
3. Closed Access
Less applicable in the present case, and yet still a factor in Windows' relative insecurity, is the fact that its code is closely guarded by Microsoft. No matter how many developers Redmond has, it simply can't compare with the countless users around the globe constantly scrutinizing Linux's open code for vulnerabilities. Microsoft developers also don't typically tell anyone about the problems they've found until a solution has been created, leaving the door open to exploits until that happens.
I'm certainly not saying that Linux is perfect, and any business user, in particular, should still enable firewalls, minimize the use of root privileges, and keep the system up to date. They could even implement a virus scanner for Linux, such as ClamAV.
The difference, though, is that such extra measures are not simply an accepted part of computing in the Linux world--they're additional steps you can take, if you want extra peace of mind. Malware is primarily a Windows problem. Use Linux, and you can mostly forget all about it.
Originally posted at Yahoo News
Friday, September 10, 2010
Firefox patches DLL load hijacking vulnerability
Mozilla has joined Apple in being among the first to fix the DLL load hijacking attack vector that continues to haunt hundreds of Windows applications.
The open-source group released Firefox 3.6.9 with patches for a total of 15 vulnerabilities (11 rated critical), including the publicly known DLL load hijacking flaw that exposes Windows users to remote code execution attacks.
The majority of the 15 vulnerabilities in this Firefox patch batch could be exploited to launch drive-by download attacks from booby-trapped Web sites. According to Firefox, the DLL load hijacking issue only affects Windows XP users:
Firefox could be used to load a malicious code library that had been planted on a victim’s computer. Firefox attempts to load dwmapi.dll upon startup as part of its platform detection, so on systems that don’t have this library, such as Windows XP, Firefox will subsequently attempt to load the library from the current working directory. An attacker could use this vulnerability to trick a user into downloading a HTML file and a malicious copy of dwmapi.dll into the same directory on their computer and opening the HTML file with Firefox, thus causing the malicious code to be executed. If the attacker was on the same network as the victim, the malicious DLL could also be loaded via a UNC path. The attack also requires that Firefox not currently be running when it is asked to open the HTML file and accompanying DLL.
Originally posted zdnet
The majority of the 15 vulnerabilities in this Firefox patch batch could be exploited to launch drive-by download attacks from booby-trapped Web sites. According to Firefox, the DLL load hijacking issue only affects Windows XP users:
Firefox could be used to load a malicious code library that had been planted on a victim’s computer. Firefox attempts to load dwmapi.dll upon startup as part of its platform detection, so on systems that don’t have this library, such as Windows XP, Firefox will subsequently attempt to load the library from the current working directory. An attacker could use this vulnerability to trick a user into downloading a HTML file and a malicious copy of dwmapi.dll into the same directory on their computer and opening the HTML file with Firefox, thus causing the malicious code to be executed. If the attacker was on the same network as the victim, the malicious DLL could also be loaded via a UNC path. The attack also requires that Firefox not currently be running when it is asked to open the HTML file and accompanying DLL.
Originally posted zdnet
Sunday, September 5, 2010
Software Testing as a Service
 In today's unforgiving business environment where customers demand zero defect software at lower costs—it is testing that provides the opportunity for software companies to separate themselves from the competition.
In today's unforgiving business environment where customers demand zero defect software at lower costs—it is testing that provides the opportunity for software companies to separate themselves from the competition.Providing a fresh perspective on this increasingly important function, Software Testing as a Service explains, in simple language, how to use software testing to improve productivity, reduce time to market, and reduce costly errors. The book explains how the normal functions of manufacturing can be applied to commoditize the software testing service to achieve consistent quality across all software projects.
This up-to-date reference reviews different software testing tools, techniques, and practices and provides succinct guidance on how to estimate costs, allocate resources, and make competitive bids. Replete with examples and case histories, this book shows software development managers, software testers, testing managers, and entrepreneurs how proper planning can lead to the creation of software that proves itself to be head and shoulders above the competition.
Get your copy of Software Testing as a Service (Price: $71.95)
Software Testing and Analysis: Process, Principles and Techniques » Barnes & Noble.com
 The first comprehensive book on software test and analysis You can't "test quality into" a software product, but neither can you build a quality software product without test and analysis. Software test and analysis is increasingly recognized, in research and in industrial practice, as a core challenge in software engineering and computer science.
The first comprehensive book on software test and analysis You can't "test quality into" a software product, but neither can you build a quality software product without test and analysis. Software test and analysis is increasingly recognized, in research and in industrial practice, as a core challenge in software engineering and computer science.Software Testing and Analysis Process, Principles, and Techniques is the first book to present a range of complementary software test and analysis techniques in an integrated, coherent fashion. It covers a full spectrum of topics from basic principles and underlying theory to organizational and process issues in real-world application. The emphasis throughout is on selecting a complementary set of practical techniques to achieve an acceptable level of quality at an acceptable cost.
Highlights of the book include
* Interplay among technical and non-technical issues in crafting an approach to software quality, with chapters devoted to planning and monitoring the software quality process.
* A selection of practical techniques ranging from inspection to automated program and design analyses to unit, integration, system, and regression testing, with technical material set in the context of real-world problems and constraints in software development.
* A coherent view of the state of the art and practice, with technical and organizational approaches to push the state of practice toward the state of the art. Throughout, the text covers techniques that are suitable for near-term application, with sufficient technical background to help you know how and when to apply them.
Exercises reinforce the instruction and ensure that you master each topic before proceeding. By incorporating software testing and analysis techniques into modern practice, Software Testing and Analysis Process, Principles, and Techniques provides both students and professionals with realistic strategies for reliable and cost-effective software development.
Get your copy of Software Testing and Analysis (Price: $61.58)
Thursday, September 2, 2010
Webcam software senses motion, sounds siren, captures images, records video, and sends captured images by e-mail
I'm using webcamera software. I
can webcast Internet video to watch my site
from anywhere.
With my new
web camera software, I can run a broadcasting tv station
of my site visible online. This opens up a number
of possibilities, the surface of which has not even been scratched in today's world. I can use
this webcast for surveillance purposes, allowing me to watch what's going on in my home
at any moment from a remote viewing computer.
As long as I have the camera
running and a remote computer with Internet access, I can watch the home.
With the software and the webcam, I can change the options to capture picture,
detect motion (if I don't want to keep the camera running at all times),
or use a combination of a online feed and recorded video to realize a security
system that takes full benefit of modern technology.
With a capture card,
I can simply move appropriate video and screenshots to use on
any station.
With sensitive files on my computer
and valuable belongings in my apartment,
it only makes sense to have a security setup that I can monitor whenever I feel that my privacy
is being compromised. If I owned a small business or lived with roommates, I couldn't imagine
living without it.
Webcam software identifies movement, triggers
siren, captures snapshots, records video, and sends captured images by email
are not bad for more than just making ip communications
more realistic. They can furthermore be
an enormously helpful tool
for exploit in house or industry protection.
title="Web camera software senses movement, sounds alarm, captures snapshots, records video, and sends captured images by email">
Application
is now accessible that can sense movement and use
it as a trigger for different events.
The way that
it works is to study the picture sent by a webcam that is either connected by USB
or using a video capture device for movement. While it picks up
that movement, it can after that take any number of actions,
including triggering an alarm.
A more popular application, though, is to either
send live frames of what is happening in the field that is covered by the camera
or to even broadcast via live streaming exactly what is
happening with both audio and picture. If installed stealthily,
this software could even be used for covert surveillance.
Given the
large amount of systems that either have a webcam connected
or can support one, this is an perfect way to inexpensively and easily defend
the spot around that property
from infringement or robbery.
New professional surveillance software works with
any web camera, IP cameras, and major capture cards.
Surveillance software
has become so difficult that the regular
businessman who has been busy minding his store instead of pouring over electronics and internet
know-how articles can be easily overwhelmed when it comes time to setup or renew his security system.
Fortunately, there is new professional surveillance software that simplifies much of the decision making.
You don't necessarily have to get rid of a working analog closed circuit TV system in order to modernize to a streaming
video that can be watched from any ip connected pc or 3G phone. Video capture cards can digitally convert the
snapshots for webcast. Until recently, there had been no real attempts to regulate the new IP
cameras; every make and manufacturer functioned a tiny differently. And when you connect webcams into the
merge, finding one software to control them all was cumbersome.
Professional surveillance software
is now available that will work for any web camera
or Internet camera and for most capture cards as well. You can supervise anything your movement
sensors are picking up at your room or firm while you can be half a globe away.
The application itself may not be easy, but it can make life simpler for you.
inSSIDer Wi-Fi Scanner
MetaGeek's InSSIDer is a great tool for finding Wi-Fi networks within range of your computer and gathering a great deal of information about each. It's also useful for troubleshooting problems with your own Wi-Fi network. For every Wi-Fi network InSSIDer finds, it shows you the MAC address of the router, the router manufacturer (if it can detect it -- it usually does), the channel it's using, the service set identifier (SSID) or public name of the network, what kind of security is in place, the speed of the network and more. In addition, it displays the current signal strength of the network, as well as its signal strength over time.
How would you use the software to troubleshoot your wireless network? If you see that your network uses the same channel as nearby networks with strong signals, you'll know that you should change the channel your network transmits over and thereby cut down on potential conflicts. (Most routers have a settings screen that lets you do this.) You can also use the software to detect "dead zones" that don't get a strong Wi-Fi connection. Walk around your home or office with InSSIDer installed on your laptop to see where signal strength drops. You can either avoid using a computer in those spots or else try repositioning the wireless router to see if it helps with coverage. Whether you need to troubleshoot a network or find Wi-Fi hot spots to which you want to connect -- or you're just plain curious -- this is one app you'll want to download and try.
What's Unique about inSSIDer?
* Use Windows Vista and Windows XP 64-bit.
* Uses the Native Wi-Fi API.
* Group by Mac Address, SSID, Channel, RSSI and Time Last Seen.
* Compatible with most GPS devices (NMEA v2.3 and higher).
How can inSSIDer help me?
* Inspect your WLAN and surrounding networks to troubleshoot competing access points.
* Track the strength of received signal in dBm over time.
* Filter access points in an easy to use format.
* Highlight access points for areas with high Wi-Fi concentration.
* Export Wi-Fi and GPS data to a KML file to view in Google Earth.
Price: Free
Compatible with: Windows XP, Vista and 7 (32- and 64-bit)
Download inSSIDer Wi-Fi Scanner (2.24MB Free)
Labels:
network scanner,
wif-fi tools,
WLan
Subscribe to:
Comments (Atom)